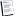 Bogus IP Header Length Packet Sniff
Bogus IP Header Length Packet Sniff
I am currently in Asia and have always had issues connecting here during working hours. This is mostly due to a terrible internet connection. In order to determine if my connection has been dropped from the server, I run wireshark to watch the IP traffic. Since the patch earlier today there has been a change in the traffic flow and new behavior in the client. After pressing Play Everquest from the server select screen, the loading icon appears on the cursor but the screen never changes. Wireshark spams the traffic pictured below. Eventually the client returns to login screen. I will try back later outside of working hours when my connection improves to see if the same results occur. This was enough of a deviance from the baseline that I wanted to share. It would be great to get a collection of packet logs from people who have similar connection issues (blank server select, crashing on zone, timeout at login, failure to load from char select) so we could compare.
Update: Was able to login after a few more tries, still curious to know what could have changed to see that new message though. Have not seen that occur in over a month of sniffing when I log in
| 
